In this article, I review activity of addresses that were exposed as Russian Government and reconstitue the timeline.
feel free to share this article or drop a message with your feedback!
An accidental discovery
Categorizing payloads on the Blockchain
A few days ago, I decided to categorize the protocols and encoding used with a specific (namely OP_RETURN) payload storage method inside the Bitcoin blockchain:
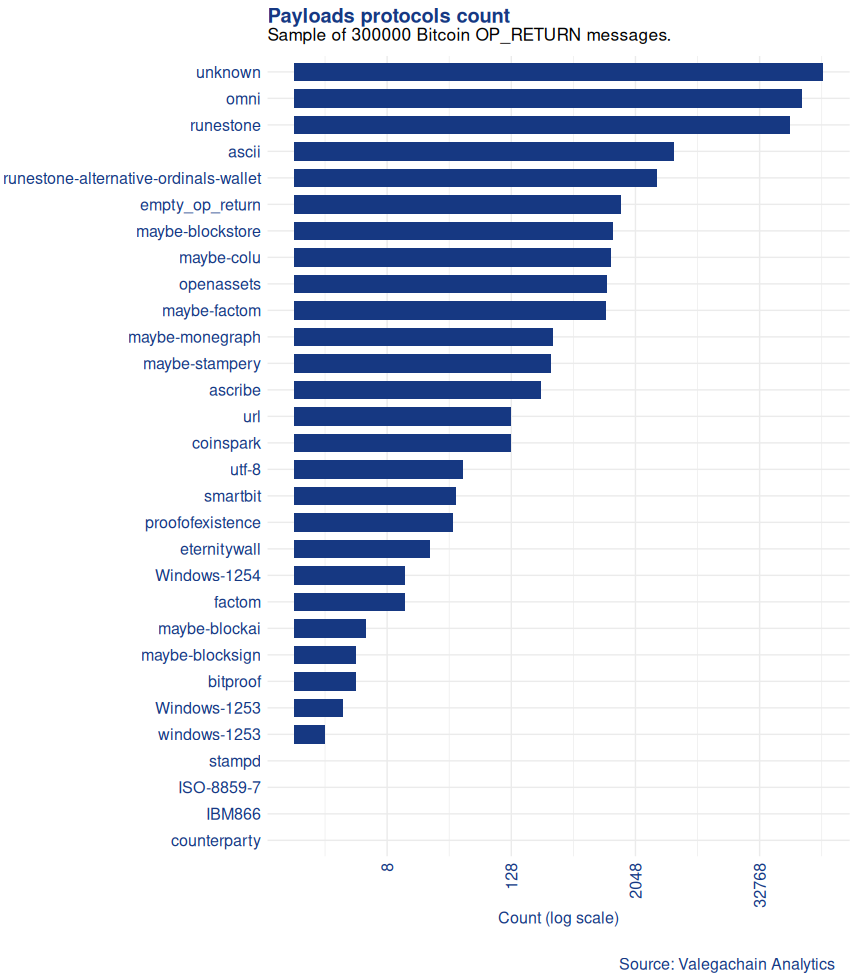
My protocol detection was still incomplete, and I decided to take a closer look at the utf8 encoded messages for new protocols I had not yet parsed:
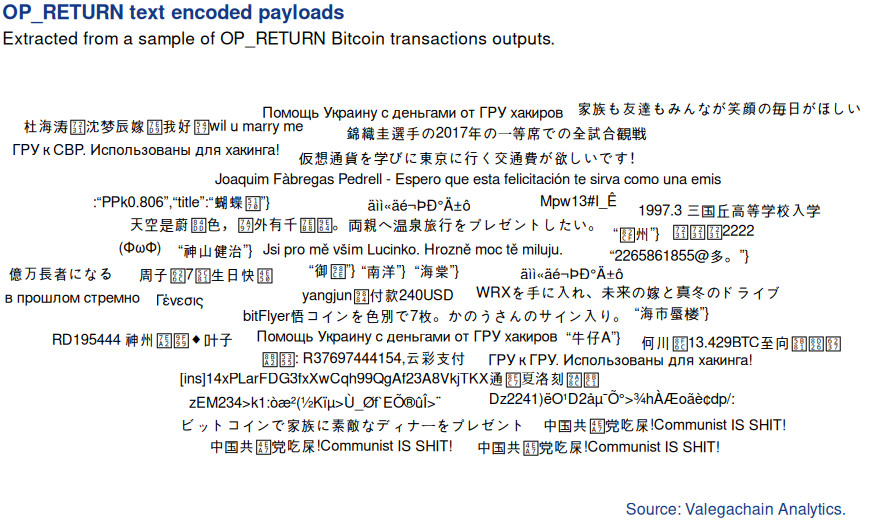
A message written in cyrilic alphabet caught my attention: ГРУ к ГРУ. Использованы для хакинга!, which is Russian for: The Main Intelligence Agency is used for hacking!, or GRU to GRU. Used for hacking!. Some Russian speakers I reached out to, when showed this message, stated that it was not proper Russian, while some others claimed that given the context, it could be kind of OK. What I understood later was that they were referring to the source (GRU) and destination (GRU) wallets in the transactions, and that a few variations of that messages are existing across numerous transactions.
Media coverage
I immediately recalled a series of articles about supposedly GRU wallet hacks from last year. The articles mentioned that Chainalysis had noticed such messages, but it was not clear which address or messages it was about.
Chainalysis is the first cypto forensic company that ever existed. It was created by Kraken's early employees, and started by collaborating with US authorities on the MtGox case. Since then, they have been maintaining strong ties with the US Government. It is very often in contract with police services all around the world. For example, some of the french police forces relies on their services.
Chainalysis originally published an article, but it seems that they took it down. Other articles referred to the Chainalysis one and shared interesting information:
The SVR used two of the wallets to “purchase infrastructure” in the SolarWinds hack, and the third was associated with a 2016 disinformation campaign targeting the Democratic National Committee with DCLeaks.com where the GRU dumped almost 20,000 emails, under an alias Guccifer 2.0.
So these addresses belonged to group of hackers that are suspected to be Russian, and were supposedly used in 2019 to fund illicit hacking activities. The following picture was also shared, which claim that the wallet actually donated Bitcoin to Ukrainians for war more recently:
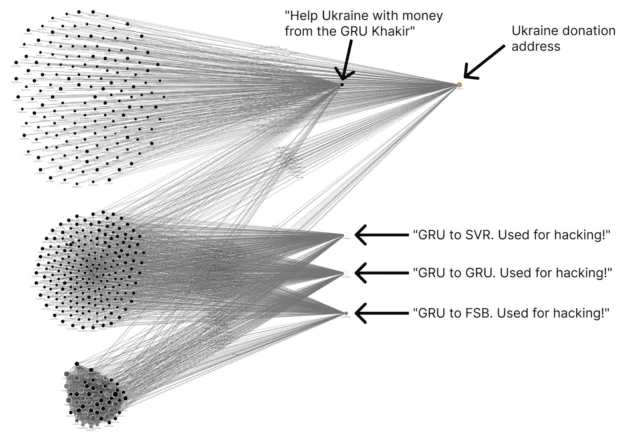
We define wallets as a set of addresses operated by the same software. Every wallet uses for change management and privacy reason multiple addresses different than the public facing one that you generally received crypto on.
Diving into the tagged transaction
Many transactions bear these inscriptions, we will mostly look at a single one here.
The transaction format
The first transaction I found with this message, 0x54303c375f2b358d5b3fb5fb15b5f4e860d73ca44e5b66f3491915a81774d13f, was in the following format (screenshot from mempool.space):
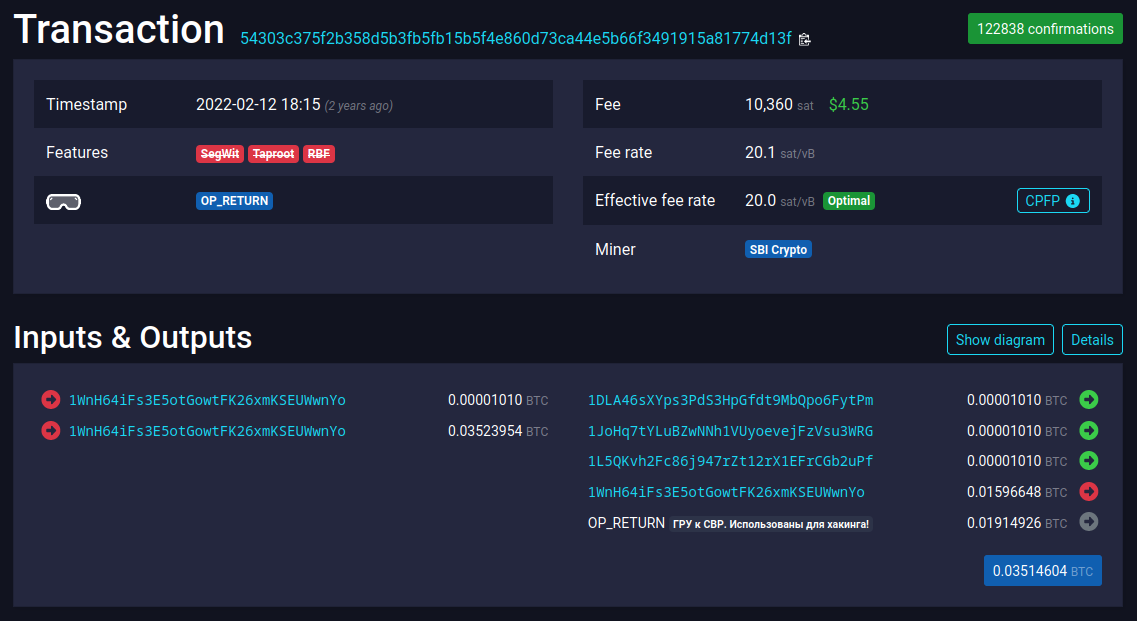
We can see that an address (1WnH64iFs3E5otGowtFK26xmKSEUWwnYo) funded a transaction in 2022, and this address is owned by the person inscribing the message. The transaction has 5 outputs:
- 3 dust amounts sent to various addresses who were never spent.
- One change output that returned the change back to the input address.
- One unspendable output with a message reading:
ГРУ к СВР. Использованы для хакинга!(GRU TO SVR, used for hacking.).
While at first glance we could assume that the text message was pointing at the 3 addresses receiving dusts, it becames clear when looking at other transactions from input and output addresses that first, they all were designated by the same kind of message, and secondly the message contains information about the sender (GRU here) and the recipient (SVR here). Unless the owners of those addresses wanted to expose themselves (with potentially false information), it effectively look just as if the addresses owner had changed.
Summarizing input and output addresses activity
Input "GRU" address 1WnH64iFs3E5otGowtFK26xmKSEUWwnYo
It has received a total of 31209662 satoshis (4.3k€ at transaction time) and spent the same (valued 2.3k€ at transaction time). More than half of its outgoing funds passed through a wallet tagged for scams. Its own wallet has at least 6 addresses, totalling 251 transaction exchanging around 20k€.
Its wallet activity is the following:
Small activity from 2019 to mid 2020 followed by a long break, and in in 2022, intensive burst of activity with 3197 relations over a single day (when the messages started to appear in all transactions).
One of the output "SVR" address 1L5QKvh2Fc86j947rZt12rX1EFrCGb2uPf
For convenience we refer to this address as svr1 in the following section.
It has many incoming relations, due to the recent message inscribed transactions, but only 2 outgoing relations. It seems to follow the same pattern as the input address regarding the dates and volume of activity:
Its 2019 activity is the following: it sent money through an address (alias unknown) to 3QZJXwJJfbiyLEexm3jJ1JLBYjVjErU9xv (alias cashier) that aggragated 40 BTC ( 270334€ at transactions time) from various illegal activities (alias ill1, ill2, ill3 and other_illicits), and cashed out to Bitstamp, as we can see on this simplified activity graph:
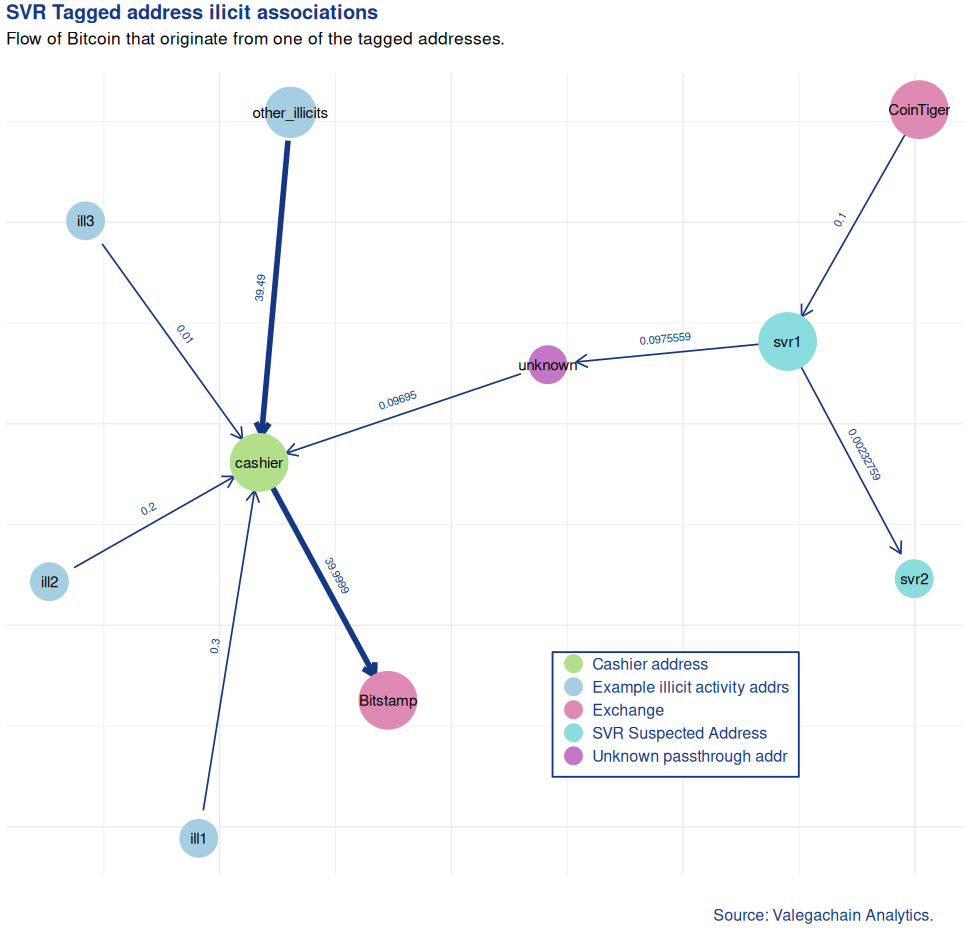
About the Bitstamp withdrawal pattern, I see a few possible explanations:
svr1was part of an organization involved in an impressive number of illegal and lucrative activies and is the owner ofunknown,cashierand other illicitssvr1ownsunknownand used a service (which operatescashier) that aggregated Bitcoins and withdraw FIAT or Monero at Bitstamp for them, maybe even using fake or stolen identity documents to register accounts on regulated exchanges. This could also be a mixing service.- Another possibility is that
unknownis not controlled by the same actor assvr1, and it actually is the personsvr1is buying a (dark?) service from.
The third option is made even more likely by the fact that svr1 sent change to svr2 when sending money to unknown, and svr2 is another address which was tagged as SVR on the blockchain and has the same activity time windows. This would means that svr1 and unknown are different wallets. Nonetheless we cannot rule out that svr1 and unknown are the same actor (whose privacy would benefit from going though multiple wallets).
Other noteworthy fact is that svr1 receives all of the 2019 incoming Bitcoins from Cointiger.com. This address or wallet was clearly purposed for a one time withdrawal and payment for unknown. Cointiger has been offline for a few month already, with the administrators claiming the following on Telegram:
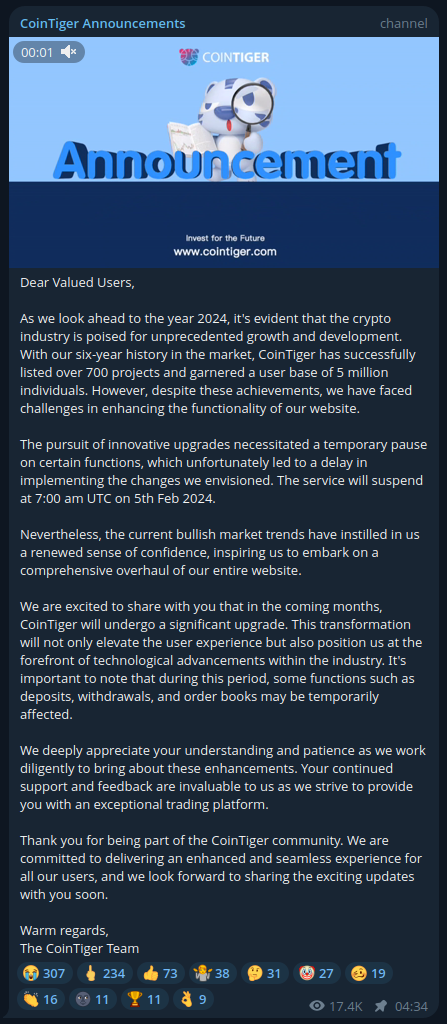
It looks like a convenient shady exchange for a group of hackers: if it ends in what look like an exit scam, this service was unlikely to be strict on KYC identity verifications.
Common patterns
Both the input and output addresses share the same two activity patterns, with sporadic high volume activity around 2019 and numerous highly connected transactions with the message in 2022. We could imagine that the first pattern was the hackers group usage, and the second would be whenever they lost the control of their server on which the wallet software resides.
Looking at the donations
We can see that the input address from the transaction we initially looked at also funded a transaction inscribed with the message Помощь Украину с деньгами от ГРУ хакиров (Help Ukraine with money from GRU hackers) that donated to an address on the kuna.io exchange, address being a known ukrainian donation addreess with over 651 Bitcoin received as of now.
The donations (including all donations that are not from these tagged addresses) started on the 24th of February 2022, the funds it received passed at one point or another in the last 30 address relations from the following entities:
- 26% passed by Binance
- 12% by FTX.com
- 12% by an unkown donating address
- Various origins of lower proportions
What can we learn from this transaction ?
When I mention SVR or GRU addresses, I refer to addresses designated as such by the messages inscribed in the transactions. These are not necessarely tied to the Russian state. Any hacker group could inscribe those messages, and decide to mislead analysts.
The facts
-
- Address within transactions inscribed with the messages are active during similar periods.
-
- The set of addresses we studied here may be from different wallet softwares, but not necessarely.
-
- We have not observed direct ties (only indirect) to known hacks or ransoms, but we only investigated a small percentage of the data available.
-
- The
GRUinput address was for sure controlled by the person inscribing the warnings as it signed transactions with those messages 2022, but theSVRones from the transaction we studied have never actually inscribed warnings or sent anything in 2022 or after. Maybe theSVRwallet was never compromised ?
- The
-
- In 2019, an
SVRaddress paid for a service in BTC, used a mixer or withdrew FIAT, and then went inactive.
- In 2019, an
-
- In 2022, for a short moment, numerous warnings were inscribed with these addresses, and donations were made to help Ukraine by the
GRUinput address.
- In 2022, for a short moment, numerous warnings were inscribed with these addresses, and donations were made to help Ukraine by the
Conclusion
It is possible that these wallets were used by hacker groups in 2019, and then in 2022 either were used for (expensive) trolling, or were hacked and exposed. If recent hacking there were, the GRU wallet was compromised, but not necessarely the SVR addresses from our transaction. The timeline from past activity also matches that of the Solarwind hack, which would corroborate what Chainalysis was publishing.